Cyber Challenges

Why is Cybersecurity hard
Resources And Talent Constraints:
- Most companies do not have the resources to research, design, architect, and implement technology solutions, or adding required controls that tie back to security.
- Even if control gaps or weaknesses are identified, the urgency and affordability of solutions would require skilled and capable workforce becomes the immediate next challenge.
Why Would Attackers Want To Target Me:
- Surprisingly, there are companies that have not recognized cybersecurity as a business need and the scale of investment needed.
- Cybersecurity is often overlooked due to budget constraints and the belief that it doesn’t apply. Many think they’re too small to be targeted.
What Is The Right Balance:
- How best to balance your level of security with the usability and affordability of your technology and process. Too much security makes things very difficult to use, make things easy to use generally means you are sacrificing security.
- How will this program interact with that security tool? How will this setting effect my customer or employee. Will these two security tools work together or fight one another?
- Everyone deals with security as a mix of affordability and complexity level in technology.
Hack statistics
- Forecasts show businesses will lose approximately $10.5 trillion in 2025 at an estimated $19,977,168 per minute due to cybercrime. (Cybercrime Magazine)
- A majority of cyberattacks are motivated by financial gain, nearly 86%. The second leading motivator of a cyberattack includes state espionage. (Verizon)
- Public companies lose an estimated 8.6% of their value after a cyber breach. (Comparitech)
- Ransomware costs for 2023 are projected to reach $30 billion globally. (Business Insurance)
- Estimates suggest in 2022 a ransomware attack took place successfully every 40 seconds, with an attempt nearly every 11 seconds. (DataProt)
- 42% reported their cyber insurance did not cover all their losses from a ransomware attack. (Cybereason)
- 560,000 new pieces of malware are discovered every day. (DataProt)
- Malware attacks cause an average loss of 50 days in time for businesses. (Privacy Sharks)
- There will be nearly 3.5 million open cybersecurity jobs waiting to be filled in 2023. (Cybersecurity Ventures)
- Average payment with a ransomware attack increased 71% in 2022 to reach $925,162. (Palo Alto Networks)
- LinkedIn phishing messages make up 47% of social media phishing attempts, mainly from fake direct messages. (Swiss Cyber Institute)
- Research from CSO Online shows that nearly 95% of all malware attacks are delivered via email. (CSO Online)
- The majority of malware attacks took place in North America, with over 80% executed as automated bot attack. (Statista)
- GDPR non-compliance fines hit nearly $100 million in the first half of 2022 alone. (AtlasVPN)
- 2 out of 3 adults in the world believe corporations have too much control over their personal data. (YouGov)

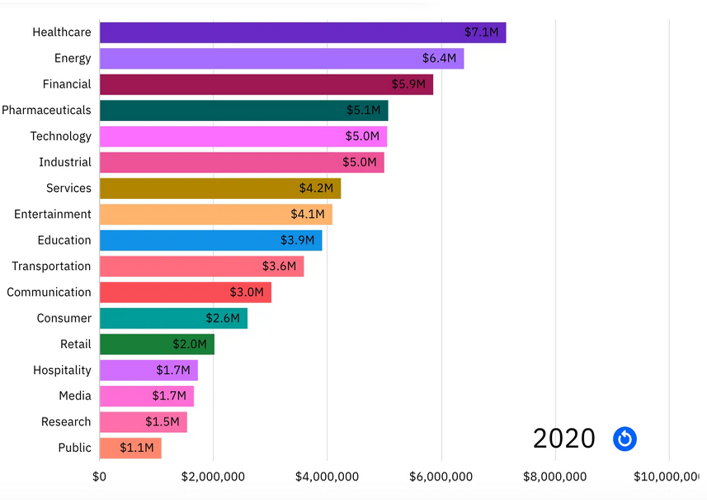
Cost of data breach (Ponemom Institute)
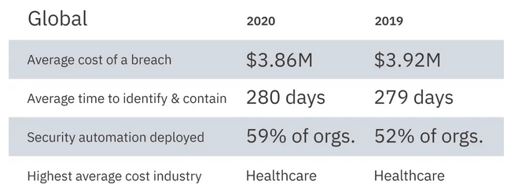
- $8.64M. United States has the highest country average cost
- $137k. Remote worker impact on average cost of a data breach
- 25,575. The average number of records affected per breach
- $150. Customer PI has the highest cost per record. $242 for US.
Global Cyber Risks Prediction
1.Speed of cloud adoption
2.Phishing and social engineering
3.Greater privacy and regulatory pressures
4.Increased demand for third-party risk management
5.Cyber insurance will drive demand for risk assessments
6.Missing (and exploitable) patches
7.Unprotected files scatter about
8.Attract and retain talent in a tightening market
9.Cyber attacks by nation states
10.Crime as-a-service
11.Smart devices as a hacking target
12.Zero Trust Replaces VPN
13.AI and machine learning
14.Multiple threat vectors used in attacks
15.Lack of cyber security knowledge
16.Credential compromise
17.Unacknowledged (or unresolved) web flaws
18.Weak incident response procedures
